Blog
Bitcoin-Wallets: What you should definitely know
Bitcoin wallets are essential tools for the secure storage and management of Bitcoin. There are different types of wallets, each of which has different advantages and disadvantages.The most important types of Bitcoin wallets and their features are described in detail below.1. Software wallets:Software wallets are programs that are installed on a computer or mobile device. They come in various forms: Desktop wallets, mobile wallets and web wallets.-> Desktop walletsDesktop wallets are installed on a PC or laptop and offer users full control over their Bitcoin. Advantages: - Ease of use: they offer a user-friendly interface and various functions for managing Bitcoin. Disadvantages: - Vulnerability to malware: If the computer becomesinfected with malware, the Bitcoin can be stolen. The Bitcoin is only as secure as the computer is.- Device dependency: If the device is lost ordamage to the device, access to the Bitcointo the Bitcoin can be lost unless backups have been created.-> Mobile walletsMobile wallets are apps that are installed on smartphones and allow users to manageusers to manage Bitcoin on the go. Advantages: - Portability: You can manage Bitcoin anywhere and at any time.- User-friendliness: Often designed to be very user-friendly. Disadvantages: - Security risks: Smartphones are vulnerable to hacking andvulnerable to hacking and malware due to the internet connection.- Risk of loss: If the cell phone is lost or stolen, the Bitcoin could also belost if no security measures such as backup and encryption have been taken.-> Web walletsWeb wallets are online services that enable access to Bitcoin via a web browser. Advantages: - accessibility: you can access theBitcoin from anywhere as long as there is an internet connection.- Easy to set up: No download or installation required. Disadvantages: - Low security: as the private keys are stored on the provider's servers, there is an increased risk of hacking and fraud.- Dependence on the provider: In the event of a service failure or fraudulentfraudulent activities of the provider, the Bitcoin can be lost.2. Hardware walletsHardware wallets are physical devices that have been specially developed for the secure storage of Bitcoin. They store the private keys offline. Advantages: - High security: As the private keys never come into contact with the Internet, they are protected against online attacks. The security of hardware wallets lies in their architecture. As they work offline thanks to a special secure element, i.e. they are not connected to the Internet, hackers cannot gain direct access to the private keys. Even if a usertransactions, the signature process is carried out offline on the device and only the signedand only the signed transaction is transmitted online. This“cold storage” method significantly minimizes the risk of theft through online attacks.- Protection against malware: Even if the computer is infected with malware, the private keys remain secure.- Ease of use: Many hardware wallets offer a user-friendly interface and simple transaction processing. Disadvantages: - Cost: Hardware wallets are significantly more expensive compared to software wallets.- Complexity for beginners: The initial setup can be a little more complicated for beginnerscomplicated for beginners, as they have to make a note of the Bitcoin seed offline.offline.3. Paper walletsA paper wallet is a physical copy or printout of the private and public keys of a Bitcoin address. Advantages: - High security: As it is a physical document, there is no digital point of attack when it is used.- Free of charge: There are no costs for thecreation of a paper wallet. Disadvantages: - Risk of loss: If the paper is lost or damaged, the Bitcoin cannot be recovered.- Cumbersome to use: Transferring Bitcoin to a paper wallet or spending Bitcoin requires additional steps and can be complicated for beginners.- No flexibility: It is more difficult to spend Bitcoin from a paper wallet as this requires importing the keys into a software wallet.- Dependence on the production provider: Generating the paper wallet requires trust in the provider that offers the production of paper wallets.Experience from the Bitcoin space:Most people in the Bitcoin space use cell phone wallets for everyday payments. The Wallet of Satoshi is recommended for beginners and the Phoenix Wallet for advanced users. Bitcoiners hold roughly the same amount of Bitcoin there as they do in cash in their wallets. Almost all Bitcoiners use a hardware wallet for their savings. The Bitcoin Only version of Bitbox is particularly recommended, as it has certain advantages over other hardware wallets. Paper wallets can be used for gifts to relatives, where, for example, €50 in Bitcoin can be given as a gift.Conclusion:Each type of Bitcoin wallet has its own advantages and disadvantages. The choice depends on the individual needs andsecurity requirements. While software wallets are practical anduser-friendly, hardware wallets offer the highest level of security by storing the private keys offline. Paper wallets can also be a secure option, but require careful handling and storage. Get your BitBox for maximum security
Learn moreThe story of the creation of Bitcoin
The emergence of Bitcoin is closely linked to the banking crisis of 2008 and the early ideas of the so-called cypherpunks for digital cash. The combination of these two factors contributed significantly to the creation of Bitcoin. The banking crisis of 2008: The banking crisis of 2008 was one of the worst financial crises in modern history. It was triggered by a combination of risky lending practices, real estate bubbles and a lack of regulation. As a result of this crisis, many people around the world have been confronted with the shortcomings of the traditional financial system, which was controlled by a few banks and governments. The role of the cypherpunks and the emergence of Bitcoin: The cypherpunk movement emerged at the beginning of the 1990s, when some libertarians and freedom-loving cryptographers and computer scientists such as Timothy May, Eric Hughes and John Gilmore began to meet on a monthly basis for a kind of get-together. The meetings consisted of discussions on various aspects of cryptography. The group's ideas culminated in "A Cypherpunk's Manifesto", a manifesto by and for cypherpunks, written by founding member Eric Hughes. A must-read for anyone trying to understand the philosophies of the cypherpunks. The cypherpunks' meetings eventually led to a mailing list. This now legendary mailing list already used the early Internet or emails. The mailing list grew significantly in the following years. Well-known personalities such as Julian Assange, Hal Finney (the first recipient of a Bitcoin transaction) and Adam Back (the first person to know about Bitcoin - apart from the inventor himself) joined the list. The discussions between group members always varied. Concerns about online privacy were commonplace, with the possibility of a burgeoning Big Brother state the greatest fear of some cypherpunks. There were also further philosophical debates and of course the exchange of ideas for a decentralized currency on or through the Internet. The release of the Bitcoin white paper: When the user with the pseudonym “Satoshi Nakamoto” also published his famous white paper entitled: “Bitcoin: A Peer-to-Peer Electronic Cash System” on the Cypherpunk mailing list in October 2008, shortly after the height of the banking crisis, he pulled initially received a lot of criticism from skeptics. Satoshi Nakamoto continued and, despite all the critics, he mined the very first Bitcoin block on January 3rd, 2009. Since this day, the Bitcoin blockchain has been running continuously. In the first block of Bitcoin, the so-called genesis block, there was the headline: "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks." This headline is from the front page of the British newspaper "The Times" on January 3, 2009. It was inserted into the genesis block by Satoshi Nakamoto and served as a kind of timestamp that gives the context of the creation of Bitcoin in connection with the banking crisis and the associated massive expansion of the money supply in 2008. The white paper presented a solution to the problems of the traditional financial system by describing a decentralized peer-to-peer payment system based on cryptography. Previous attempts at digital cash: Before the emergence of Bitcoin, there were several attempts to develop electronic cash. Some of these attempts were more experimental and did not have a major impact, while others attracted some attention but were ultimately unsuccessful. Here are some of the notable examples: 1. E-Gold (1996): E-Gold was one of the first successful electronic payment systems, allowing users to buy, sell and transfer gold. Founded in 1996 by Douglas Jackson and Barry Downey, it was based on a reserve of physical gold held on behalf of users. Although E-Gold was successful in its early years, it was later shut down due to abuse for illegal activities. 2. HashCash (1997): HashCash was developed by Adam Back as a means to combat email spam by using a proof-of-work mechanism. However, it was also intended as an electronic payment system. HashCash later inspired Bitcoin's proof-of-work mechanism. 3. B Money (1998): Proposed by Wei Dai, B-Money was a theoretical concept for a decentralized digital currency. It was based on cryptographic techniques and a peer-to-peer network similar to Bitcoin. 4. Bit Gold (2005): Bit Gold was a concept for a digital currency based on cryptographic techniques and a decentralized protocol proposed by Nick Szabo. Although Bit Gold was never implemented, it is often considered a precursor to Bitcoin. These projects laid the foundation for the development of Bitcoin by exploring various concepts and ideas to create a decentralized digital currency. Satoshi once commented on these projects by saying, "Many people automatically reject electronic currencies as a lost cause because of all the failures of the companies since 1990. I hope it is obvious that the reason for this was the centrally controlled nature of these projects that they were doomed to fail." Bitcoin ultimately combined many of the ideas from these early concepts and brought them together in a uniformly functioning, open-source system that was accessible to everyone. In 2011, Satoshi's last sign of life was finally noticed. "I've moved on to other things," Satoshi wrote to software developer Mike Hearn on April 23, 2011. After that, Satoshi disappeared and became a myth. The creation of Bitcoin as a response to the crisis: The banking crisis of 2008 ultimately served as a catalyst for the creation of Bitcoin. The combination of the flaws of the traditional financial system and the ideas of cypherpunks fighting for freedom led to the creation of an alternative currency. No central entity, no elite, no government in the world, no matter how powerful, is able to control Bitcoin. Anyone can view the code and check for errors. Anyone can develop and operate Bitcoin. Bitcoin is everyone's money, freedom money. Bitcoin was born as a response to the crisis, with the aim of creating a transparent, secure, decentralized form of digital cash with a limited supply of 21 million Bitcoins. Since its creation, Bitcoin has stood for freedom of the individual, personal responsibility and privacy on the Internet. Discover your Bitcoin miner for home
Learn moreThe Lightning Network: The Future of Bitcoin Transactions
Bitcoin was released in 2009. Since then, the community of people interested in Bitcoin has continued to grow. However, there have also been criticisms of Bitcoin since its inception, such as the lack of scaling options, potentially expensive fees on the main network and the lack of privacy in payments. The so-called Lightning network was ultimately created to address these problems. The Lightning Network was first proposed and developed in 2015. However, there were different stages of development. The implementation and introduction took place gradually over the years. What is the Lightning Network? The Lightning Network is a so-called "second layer" or "off-chain" solution for the Bitcoin network, which was created, among other things, due to the blockchain trilemma. Blockchain trilemma The blockchain trilemma describes the fact that a distributed database, such as Bitcoin, can only maximize two of the three properties of security, decentralization or scalability. It is considered impossible for a blockchain to be decentralized and secure and still be extremely scalable. If a blockchain attempts to scale by increasing the size of the blocks in the blockchain, the costs of operating a so-called fullnode (a computer that stores the entire blockchain and validates the transactions) increase. The larger the blocks in a blockchain, the greater the bandwidth, processing and storage requirements for each individual full node. Increasing the transaction capacity and the associated increase in the size of the blocks would have the undesirable effect of centralizing the system, as only large companies and no private individuals could afford to operate a full node. Blockchain and Lightning easy to understand Imagine the Bitcoin network as a classroom filled with students. If you want to send a classmate a Bitcoin, you both stand up, tell all the other students that you want to make this transaction, and all the other students will write this transaction down in their notebooks. This is therefore not only time-consuming, but also expensive and is not really anonymous. If you want to use the Lightning Network, think of it as telling all students that you and your classmate will be leaving the classroom. All students write down how many Bitcoin you and your classmate leave the classroom with. Outside of the classroom, you can now send transactions to your classmate and back billions of times per second, without any fee, without anyone knowing. When you decide that you no longer want to transact with your classmate, you both come back to the classroom and tell all students how many Bitcoin you each have left. Now all students write this down again. How does the Lightning Network work technically? At its core, the Lightning Network enables transactions to be carried out outside of the blockchain. This is done by opening a so-called “payment channel” between the parties involved. Instead of writing every single Bitcoin transfer to the blockchain, users can make a series of transactions directly between themselves and share the transaction data with each other. Only when the payment channel is closed is the final transaction data written to the blockchain. Advantages of the Lightning Network: 1. Speed : Transactions on the Lightning Network are implemented almost instantly, in contrast to the slower transaction times on the Bitcoin blockchain. 2. Cost efficiency: Since transactions are carried out outside the blockchain and no proof of work in the form of mining is required, fees are significantly lower in the cent range. 3. Scalability: The Lightning Network allows Bitcoin to process a much larger number of transactions without overloading the blockchain. Technically, Lightning does not have a maximum number of transactions that can be made per second. 4. Micro-transactions: The Lightning Network opens up new possibilities for micro-transactions, as transactions can theoretically be carried out in cents and every second. An example is streaming for Bitcoin podcasts, which are billed in Satoshis per second. 5. Privacy: Since transactions occur off-blockchain within private payment channels, they are private and are not publicly recorded. How to use the Lightning Network? To use the Lightning network, you need a Lightning-enabled Bitcoin wallet such as the Wallet of Satoshi or the Phoenix Wallet, which can be downloaded from the Android or Apple store. These wallets support sending and receiving payments via the Lightning Network. Once you have such a wallet, you can send and receive payments to other Lightning users. Is it already used a lot? The use of the Lightning Network has become increasingly widespread in recent years. Especially in countries where people are suffering more from the current monetary system, they are looking for alternative payment methods. One example is the people from El Salvador, many of whom work in the USA and whose remittances back home make up a large part of El Salvador's gross domestic product. Until now, these people had to rely on expensive channels such as Western Union, whereby the transactions not only sometimes included 20% fees, but also took several days. With Lightning, these people now have almost no fees when sending the money they have earned, are not dependent on a third party like Western Union and can send money to their home country peer-to-peer within a second. Challenges and future prospects: Although the Lightning Network is promising, there are still some challenges ahead. These include the ease of use of wallets, the reliability of payments and acceptance by the general public. Nevertheless, developers around the world are continually working on improvements to make the Lightning Network even more robust and beginner-friendly. Conclusion: The Lightning Network is an exciting development that has the potential to make Bitcoin an even more useful and versatile means of payment. Through its ability to make transactions fast, inexpensive and scalable, the Lightning Network could make a major contribution to the further adoption of Bitcoin as money. Discover the Bitcoin miner for your desk
Learn moreIs a 51% attack on Bitcoin possible?
In this article we will explain what a 51% attack is, how much energy it requires and what damage it would mean to Bitcoin. What is a 51% attack? A 51% attack occurs when a group of Bitcoin miners controls more than 50% of the Bitcoin network's computing power. With this majority, they could manipulate the network by reversing transactions or double spending. This could lead to loss of trust, loss of value and other negative effects. Are mining pools capable of this? Some miners join together to form so-called mining pools, which allows them to pool their computing power. This increases the probability of finding a valid block and receiving the block reward. This is then divided among the members of the mining pool, depending on how much computing power an individual member has made available to the pool. Incentive system To understand how likely a 51% attack really is, it is necessary to understand the incentive system of Bitcoin miners. If the pools, as a group of miners, try to add an invalid block to the blockchain, it would be rejected by the network (full nodes) and the miner would therefore forego the corresponding block reward. Each miner therefore has an economic incentive to act honestly in order to receive the block reward. This is the only way a miner can cover their business costs in the long term. Mining offline There are also so-called double-spending attacks, in which malicious network participants can spend their Bitcoin multiple times. Basically not possible for mining pools. In order to secretly mine a “fake blockchain,” the pool operator would have to take it “offline” and publish the new chain at a later date to overwrite the old one. However, if the operator goes offline, the participants in the pool would immediately jump out and change it. Since this can literally be done in just a few minutes, it can be stated that pool operators actually have no power and should rather be seen as service providers. Malicious miners in general would suffer financial damage anyway, because the mining hardware purchased for the attack would also quickly lose most of its value. Due to the enormous capital costs, there is no economic incentive for a 51% attack. Every network participant would suffer financial damage. Only an attacker who attempts to attack the network with a self-destructive motive could become a threat to the network. However, this attack would involve enormous amounts of economic resources. However, this is unrealistic for mining pools, as it cannot be assumed that all pool participants want to harm the network. Rather the opposite. Example Ghash.io In 2014, Ghash.io controlled more than 50% of the hashrate. The pool's miners could therefore have carried out a 51% attack. Even back then, this situation unsettled the Bitcoin community. But the economic incentives prevailed. Ghash.io released a statement asking miners to leave the pool so that the pool's share falls below 40%. As mentioned above, a big advantage of Bitcoin miners is their flexibility. To belong to a mining pool, miners simply have to enter the so-called stratum address into the mining software and deposit a wallet for payouts. The miners complied with the pool operator's request and moved to other pools. A year later, Ghash.io's market share fell to 2%. Stratum V2 However, the Bitcoin community is aware of the potential dangers of centralizing mining pools, which is why decentralization is already underway. The most promising project is Stratum V2, a revised version of the current mining protocol, which was presented at the Bitcoin Conference 2019. With Stratum V2, miners in a pool can decide for themselves which transactions should be included in the block. This is currently the responsibility of the pool operators and thus reduces the dependency on the mining pools. Although block generation is still in the hands of the mining pools, adopting Stratum V2 would be an important step towards decentralizing the mining pools. How many miners for 51%? To successfully carry out a 51% attack, a group of attackers requires a significant amount of computing power. The exact amount depends on the current hashrate of the Bitcoin network, which is constantly changing as new Bitcoin miners join and old ones leave. Currently (March 2024) the hash rate is approximately 600 exahashes per second, i.e. 600,000,000,000,000,000,000 hashes per second worldwide, which all Bitcoin miners put together. One of the best and most popular devices for mining Bitcoin is the Antminer S19 Pro from Bitmain. The miner has a hash rate of 110 TH/s (terahashes per second) and consumes 3,250 watts of power. If we now want to know how many of these S19 Pro miners we need to get 51% of the hashrate of the Bitcoin network, we multiply the 600 exahashes by 51% and get 306 exahashes. If we now divide this by the 110 terahashes of a device, we get the number of S19 Pro: 2,781,818 devices How many nuclear power plants? How much electricity do we need? To do this, we multiply the number of devices by the 3,250 watts of a device: 9,040,908,500 watts. How many nuclear power plants would we need for this? The two reactor blocks of the Chinese Taishan nuclear power plant currently have the largest net output in the world at 1,660 MW (see Wikipedia). 1 megawatt equals 1,000,000 watts. Accordingly, 1,660 MW is 1,660,000,000 watts that the world's most powerful nuclear power plant, Taishan, can generate. Now we divide the 9,040,908,500 watts required for 51% of the hashrate by the 1,660,000,000 watts of a Taishan nuclear power plant. Result? For 51% of Bitcoin's hashrate, we need 5.44 Taishan nuclear power plants, whose electricity should not be used for anything other than Bitcoin miners. Not only would this project have to take place in secret, but the success would also only be short-lived. Right from the first block by the attacker, every user in the network would be aware through the mining data in the block that 51% of the hashing power was in the hands of an attacker. No further block would now be able to be added to the blockchain by the attacker through the nodes. The network would split and the attacker would automatically leave the network. What if the attacker knew how to hide the attack? Even if the attacker managed to ensure that not all nodes rejected his blocks directly, the attacker would have a significant problem after 2016 blocks at the latest, since the so-called difficulty adjustment takes place in the network every two weeks, which is determined by an algorithm that increases the difficulty of the block Mining is always set so that a new block is only found every ten minutes on average. Since the attacker has invested a massive amount of new energy into the network, blocks are now found much more frequently, which would lead to a massive increase in difficulty. This in turn would ensure that the time interval for finding blocks for the attacker would increase significantly. At this point it is up to each person to decide how likely such a scenario is. Your Bitcoin miner for home
Learn moreCan Bitcoin still be stopped?
Since its introduction in 2009, Bitcoin has become a global currency used worldwide. One of the most fascinating features of Bitcoin is its impossibility to be stopped or controlled. This independence from government influences and traditional financial institutions is based on several aspects that make Bitcoin the most robust and resilient network in human history. Decentralization: One aspect that protects Bitcoin from manipulation and censorship is its decentralized nature. Unlike traditional fiat currencies, which can be issued and controlled by central, corruptible central banks or governments, Bitcoin is operated by a globally distributed network of participants. Miners validate transactions, create new Bitcoin and secure the network by investing electricity. Node operators use their nodes to control the rules of the network, according to which all users and miners must behave. No central control body is able to intervene in these structures. Blockchain technology: The blockchain technology that Bitcoin uses is a public, transparent and immutable database of all transactions. Each transaction is stored in blocks that are linked to each other and form a chronological history, which is why Satoshi Nakamoto also called it a timechain. The longer a block lies in the past, the more immutable it becomes. Proof of work: Since Bitcoin mining runs on the so-called Proof of Work mechanism, users have no influence on decisions in the network by holding Bitcoin. For example, if an entity with evil intentions wanted to expand the total supply from 21 million Bitcoin to 42 million, that entity would have to engage in mining, since the miners are the ones on the network who are releasing new Bitcoin (currently 6.25 Bitcoin per block as of March 2024). . Even if this entity were able to exert more than 51% of the network's energy (51% attack), the moment the attacker publishes the first block of its own (with more than the currently valid 6.25 Bitcoin). would, no node in the network would accept this block because it does not correspond to the consensus rules of the network. The network or blockchain would split. In the well-known Bitcoin network with 21 million Bitcoin as the upper limit and in a second network with 42 million Bitcoin, in which only the attacker would operate. This is where the saying “Not your node, not your rules” comes from. If you operate a Bitcoin node as a user, you can decide which rules apply in your network. If an attacker doesn't play according to these rules, he automatically excludes himself because no one wants to "play" with him. Cryptography: Bitcoin uses cryptographic techniques to ensure the security and immutability of the network. Transactions are signed with public and private keys, making them secure and tamper-proof. The use of cryptographic hash functions ensures that any change to a block is detected immediately, protecting the network from attacks. Modern cryptography uses keys so long that it would take billions of years to crack all possible key combinations through systematic trial and error. Global acceptance and user participation: The global spread and growing number of Bitcoin users also help strengthen its independence. With an ever-growing user base and increasing interest from companies, institutions and governments, Bitcoin is becoming increasingly difficult to ignore or combat. Conclusion: Bitcoin can no longer be stopped. If a state tries to stop Bitcoin by banning it, it not only automatically makes Bitcoin more interesting for its own citizens, but the country also simply excludes itself from the global network. The only points of attack that state actors can attack are the fiat-Bitcoin gateways, i.e. the places where fiat currencies and Bitcoin are exchanged: the exchanges. These exchanges can be overloaded with bureaucracy (such as KYC or AML) or effectively banned, as they are companies that can be put under government pressure. However, the Bitcoin network itself is like an idea whose time has come: Unstoppable. Discover your Nerdminer
Learn moreAn introduction to Bitcoin mining: How does it work and why is it important?
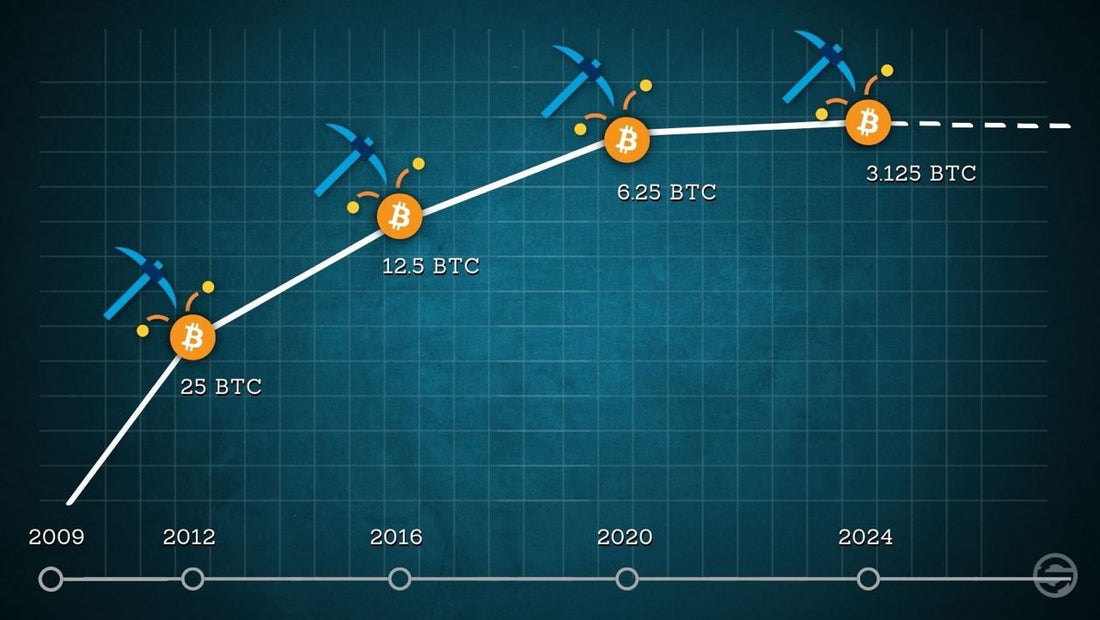
How does Bitcoin mining work?1. Collect transactions: First, the network collects unconfirmed transactions in a so-called "mempool". When a user sends a transaction, the transaction ends up in this mempool. It is comparable to a queue.2. Formation of blocks: Miners select transactions from the mempool and group them into a block. For economic reasons, they always select the transactions that generate the most fees.3. Reward for miners: Miners are rewarded for their energy expenditure with new Bitcoin. This is the mechanism that brings new Bitcoin into circulation. From 2009 to 2012 it was 50 Bitcoin per block, 2012-2016 25 Bitcoin, 2016-2020 12.5 Bitcoin, 2020-2024 6.25 Bitcoin and since the halving in April 2024 only 3.125 Bitcoin. This represents Bitcoin's monetary inflation, which was around 1.6% before the halving in 2024 and has halved to 0.8% since the halving, meaning that inflation is now lower than it is for gold.Challenges and future prospectsBitcoin miners are faced with the dilemma that halving reduces their turnover by 50% every four years. This indirectly forces miners to constantly reduce their costs as much as possible in order to achieve maximum efficiency.The biggest items are electricity consumption and hardware costs. Halving every four years means that miners are always on the lookout for cheaper electricity, which can primarily be found in unpopulated areas of the world through surplus energy, i.e. electricity that would otherwise not be purchased by anyone. ConclusionBitcoin mining is a fascinating process that ensures the integrity of Bitcoin.Discover your Nerdminer
Learn moreThe 20 most important terms in Bitcoin
Bitcoin is on everyone's lips, but getting started can be confusing with a variety of technical terms. Here are the 20 most important terms that beginners should know: 1. Blockchain: A decentralized and distributed database that stores transactions securely and transparently. 2. Cryptocurrency: A digital or virtual currency that uses cryptographic techniques for its security. 3. Bitcoin: The first and most famous cryptocurrency, introduced by Satoshi Nakamoto in 2009. Also the only decentralized cryptocurrency. 4. Altcoin: Any cryptocurrency other than Bitcoin, such as Ethereum, Ripple and Litecoin. Altcoins represent centralized or distributed networks, which, however, do not fulfill the aspect of decentralization, as a central entity always manages the network. 5. Bitcoin Wallet: A digital wallet that allows storing, sending and receiving Bitcoin. 6. Bitcoin Mining: The process in which, on the one hand, the Bitcoin network is secured and, on the other hand, new Bitcoin are created by applying energy. 7. Hash: A cryptographic function that converts data into a specified string and is used to secure information on the blockchain. 8. Smart Contracts: Self-executing contracts based on the blockchain that are automatically executed when certain conditions are met. 9. ICO (Initial Coin Offering): A financing method in which new cryptocurrencies are introduced by selling tokens to investors. 10. Fork: The fork of an existing blockchain that leads to a new version, such as hard forks and soft forks (example Bitcoin Cash) 11. Private Key: A secret key that allows one to access their cryptocurrencies and authorize transactions. 12. Public Key: A public key that allows others to send cryptocurrencies to a specific wallet. 13. Exchange: A platform where cryptocurrencies can be bought, sold or exchanged. 14. All-time high: All-time high of the price of a cryptocurrency in fiat currencies. 15. Stacking Sats: Regular saving in Bitcoin, e.g. in the form of a weekly or monthly savings plan. 16. Bitcoin Whale: An individual or group that owns a significant amount of Bitcoin and can thereby exert an influence on the price. 17. FOMO (Fear of Missing Out): The fear of missing out on a lucrative opportunity, which often leads to impulsive investment decisions. 18. Market Cap: The total value of all units of a cryptocurrency in circulation. 19. Fiat currencies: The current government-run inflationary currencies such as the dollar or euro. 20. Hardware wallet: A wallet that is not connected to the Internet and is therefore protected from hacker attacks (e.g. the Bitbox). With these basic concepts you will be better equipped to dive into the fascinating world of Bitcoin. Become a Bitcoin miner now
Learn more